Your data security, our priority
Our businesses are totally dependent on technology, which offers us great advantages but it also poses threats such as cyber-crime, whose strategies grow every day. As you would do with your office, your home or your car, you need to take security measures.
If you are reading this, it means you take this matter seriously. Check how our team of experts, who continuously collaborate with the main international agencies fighting cyber-crime, can help!

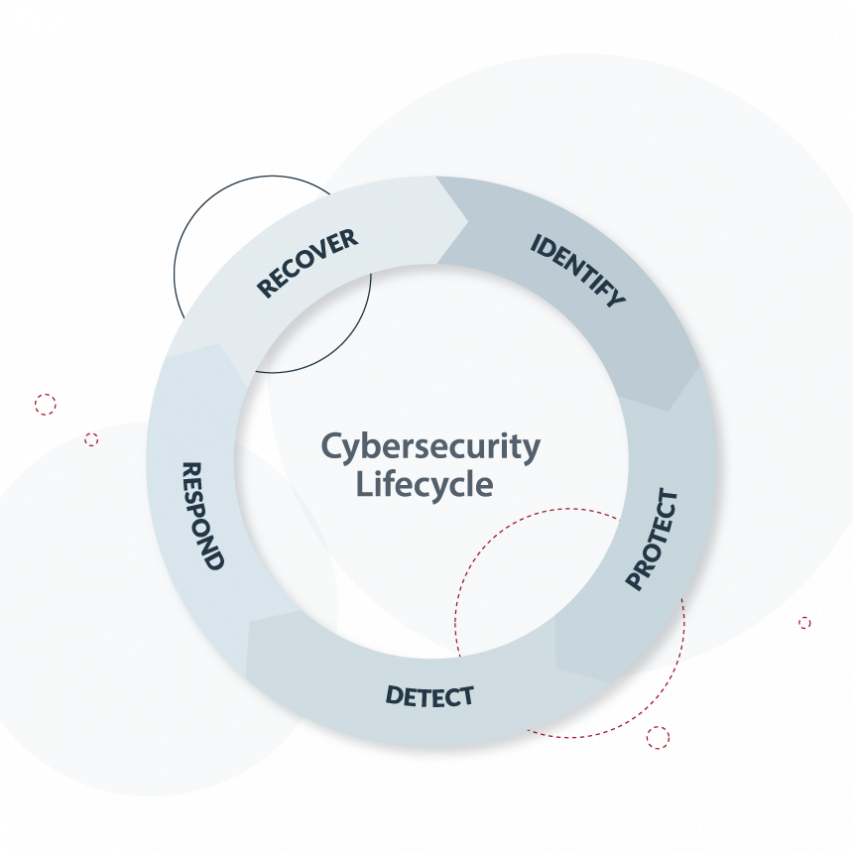
Security Operation Center (SOC)
Our main 360º and 24/7 service.
By continuously analyzing new threats and monitoring your systems’ activity, we give immediate response to ensure that your business is always secure.
We use the latest tools to trigger alerts when something unexpected is happening and depending on the situation, automatic protocols will start running or one of our experts will personally analyze it and respond accordingly.
Our SOC is composed of several specialized teams with different responsibilities to ensure every possible aspect of your security is covered by them.
Red Team
Our part of the team specialized in the analysis and simulation of attacking procedures.
To prepare a defense properly, you need to know how someone will attack. Our team will assume the role of the attacker by using the same tactics, techniques and procedures. They will find all possible vulnerabilities and exploits in your applications and systems. This will expose the risks your company is running so that our specialists may suggest ways to eliminate or mitigate those risks.
Blue Team
Our part of the team specialized in defense.
Although the blue team also knows the techniques used to attack, they are more focused on building responses to prevent, detect and mitigate those attacks. They continuously strengthen your security and monitor your systems looking for suspicious activity, and they activate defense protocols when something unusual is detected.
Audit and Consultancy
Your IT-OT infrastructure performance is not what you expected? Do you want to ensure there is no security breach in your company and you comply with current regulations? Starting with remote work and not sure how to make it secure?
These are some of the typical cases we get from our customers. Once edataconsulting receives a request, we will consider every possible risk from unsecure IT-OT infrastructure to lack of security awareness or protocols with your employees. Our audit team will perform controlled attacks, evaluate your defense and prepare a complete report plus a full information security director plan to implement within your company. This plan will ensure business continuity, data integrity, confidentiality and availability.
Application Security
Are your web and cloud applications secure?
This is a question we asked ourselves years ago. Since there are so many factors to keep in mind when assessing the security of an application and we want to deliver quality software to our customers, we perform periodical analyses and audits of:
- The code we produce
- Third-party libraries and frameworks used
- The web and application servers where the applications are deployed
- Events logs of cloud solutions used
If some vulnerability is found, a cost-effective solution will be proposed and implemented by the responsible team.

















